Experts provide the keys to deciphering today’s and tomorrow’s cryptography
Rédigé par Monir Azraoui
-
25 March 2025Cryptography has always been a cornerstone of communication and data security. What’s new in cryptography? What are the main trends in cryptography for data and privacy protection? What developments should we anticipate? To help answer these questions, we spoke with several French cryptography experts. This article highlights the key points emerging from these discussions.
In our constantly evolving, hyperconnected world, the personal data we store, process, or share online is more vulnerable than ever to cyber threats. Cryptography provides tools to protect data and communications against these threats. Beyond the goal of confidentiality that encryption aims to achieve, cryptography also plays a key role in ensuring data integrity (i.e. the data has not been altered) and authenticity (verifying the origin) through hashing functions and digital signatures.
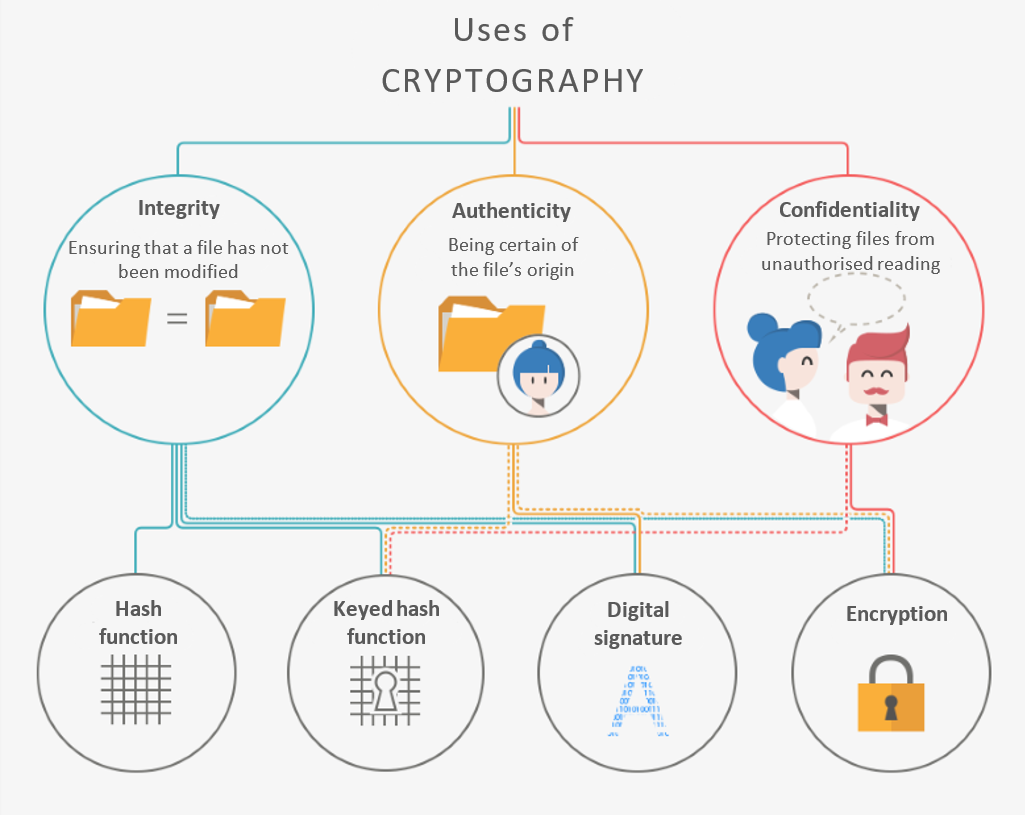
Source : https://www.cnil.fr/fr/comprendre-les-grands-principes-de-la-cryptologie-et-du-chiffrement
These tools (encryption, hashing, and digital signature) are used on a daily basis today. However, with the emergence of new digital paradigms such as the Cloud, Artificial Intelligence, and Internet of Things, cryptography had to be modernised. These new technologies have introduced new challenges in terms of security and data protection, requiring more advanced cryptographic solutions. Not only do these advancements aim to address increasingly sophisticated threats, but they also adapt to the specific needs of new digital applications.
We initiated work to explore these advanced cryptographic technologies through a series of interviews with French experts in the field:
- Olivier Blazy, Professor and researcher at École Polytechnique:
Olivier Blazy is a professor of cybersecurity at École Polytechnique in the Computer Science department. He has been a researcher in cryptography for 10 years, working on various topics including cryptography for privacy protection and post-quantum cryptography. At the national level, he co-chairs the CNRS Code and Cryptography working group within the Information Security and Computer Science-Mathematics Research Groups (GDR).
- Sébastien Canard, Professor at Télécom Paris, formerly a research engineer at Orange:
Sébastien Canard has been a professor at Télécom Paris since 2023, working with the Cybersecurity and Cryptography [C²] team. At the time of our interview, Sébastien was a research engineer since 2003 for the R&D department of the telecom operator Orange, where he was a member of the « applied cryptography » group. His research focuses, among other things, on the design of privacy-preserving cryptographic protocols.
- Melek Önen, Professor at EURECOM:
Melek Önen is a professor in the Digital Security Department at EURECOM (Sophia-Antipolis). Her research focuses on applied cryptography, information security, and privacy protection. She works on the design and development of cryptographic protocols for various technologies, including cloud computing and machine learning.
- Pascal Paillier, Co-founder and Chief Technology Officer at Zama:
Pascal Paillier is a researcher and entrepreneur in cryptography and currently serves as Chief Technology Officer at Zama. For over 25 years, his work has focused on designing and developing cryptographic techniques for sensitive industries. He is notably the designer of the homomorphic cryptographic system that bears his name. He also contributes to efforts to standardise encryption.
- ANSSI, Technical Assistance Division (Anthony Journault) et Cryptography Lab (Henri Gilbert ; Jérôme Plût ; Mélissa Rossi ; Yannick Seurin):
The cryptography lab is ANSSI's center of expertise for cryptographic algorithms, mechanisms, and architectures. In these areas, the lab is involved in research, requirement analysis, and the design of solutions to meet those requirements, as well as product evaluation and the development and updating of technical standards.
ANSSI's Technical Assistance Division is designed to assist public administrations in securing their information systems, and in the case of the experts interviewed, in projects involving cryptographic mechanisms.
We present a summary of the interviews with these experts in a series of three articles.
The first and second articles explore the four advanced cryptographic technologies that experts consider crucial to the IT security landscape:
- post-quantum cryptography,
- cryptography enabling operations to be performed on encrypted data,
- zero-knowledge proofs, and
- group signatures.
Finally, the third article presents three contexts in which these technologies can be applied:
- personal data processing,
- artificial intelligence, and
- confidential cloud computing.
It also identifies the challenges that need to be addressed in order for advanced cryptographic technologies to be adopted and used on a larger scale.
Contents
Article 1: Post-quantum cryptography
Article 2: Advanced privacy-preserving cryptographic techniques
Article 3: Practical applications of advanced cryptography
Acknowledgments
These articles would not have been possible without the support of the experts listed above, who devoted their valuable time to their experiences with us.
These articles are the result of a collective effort, and the author would like to thank his colleagues Solenn Brunet et Amandine Jambert for their essential collaboration in this work.
Illustration : Flickr


